-
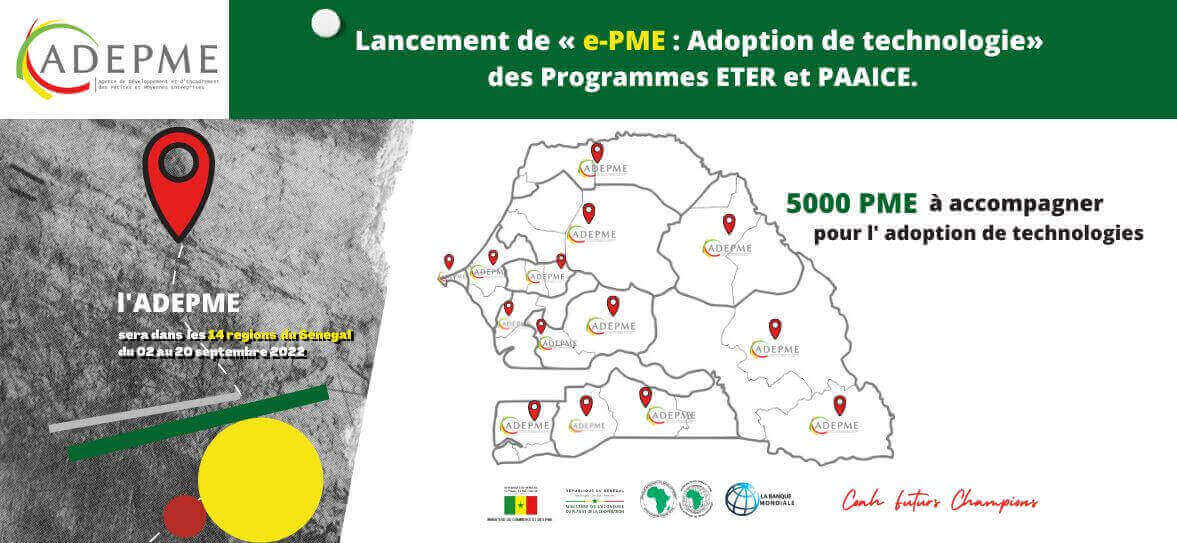
29101
PME accompagnées
-
451
PME appuyées Covid
-
8096
PME bénéficiaires du FFP
-
3323
PME formalisées
-
77927
Emplois créés/maintenus
-
18.5M
Financement mobilisé auprès des IF
-
Nos services
Améliorer votre Business
-
Réseautage
L’ADEPME multiplie les rencontres pour améliorer les connaissances mutuelles et nouer des liens professionnels forts…
En savoir plus
-
Accompagnement
L’ADEPME accompagne le porteur d’idée ou le dirigeant de PME tout au long de la vie de leur entreprise : ….
En savoir plus
-
Etudes et veille
Les études et la veille portent sur des analyses approfondies des statistiques du commerce intérieur…
En savoir plus
-
Formation et ateliers thématiques
Le renforcement des capacités des dirigeants des PME s’effectue par la formation et ….
En savoir plus
-
Conseils
L’ADEPME apporte conseils et orientations aux porteurs d’idées et dirigeants de PME. Les conseils sont variés et …
En savoir plus
-
Mécanisme de transfert de technologie ISO
Le Sénégal souffre d’une profonde dépendance vis-à-vis des pays extérieurs…
En savoir plus
-
Problem solving
L’ADEPME est un facilitateur de la relation entre l’Administration public et les PME. Elle organise des cadres ….
En savoir plus
Nos partenaires
Contactez-nous
















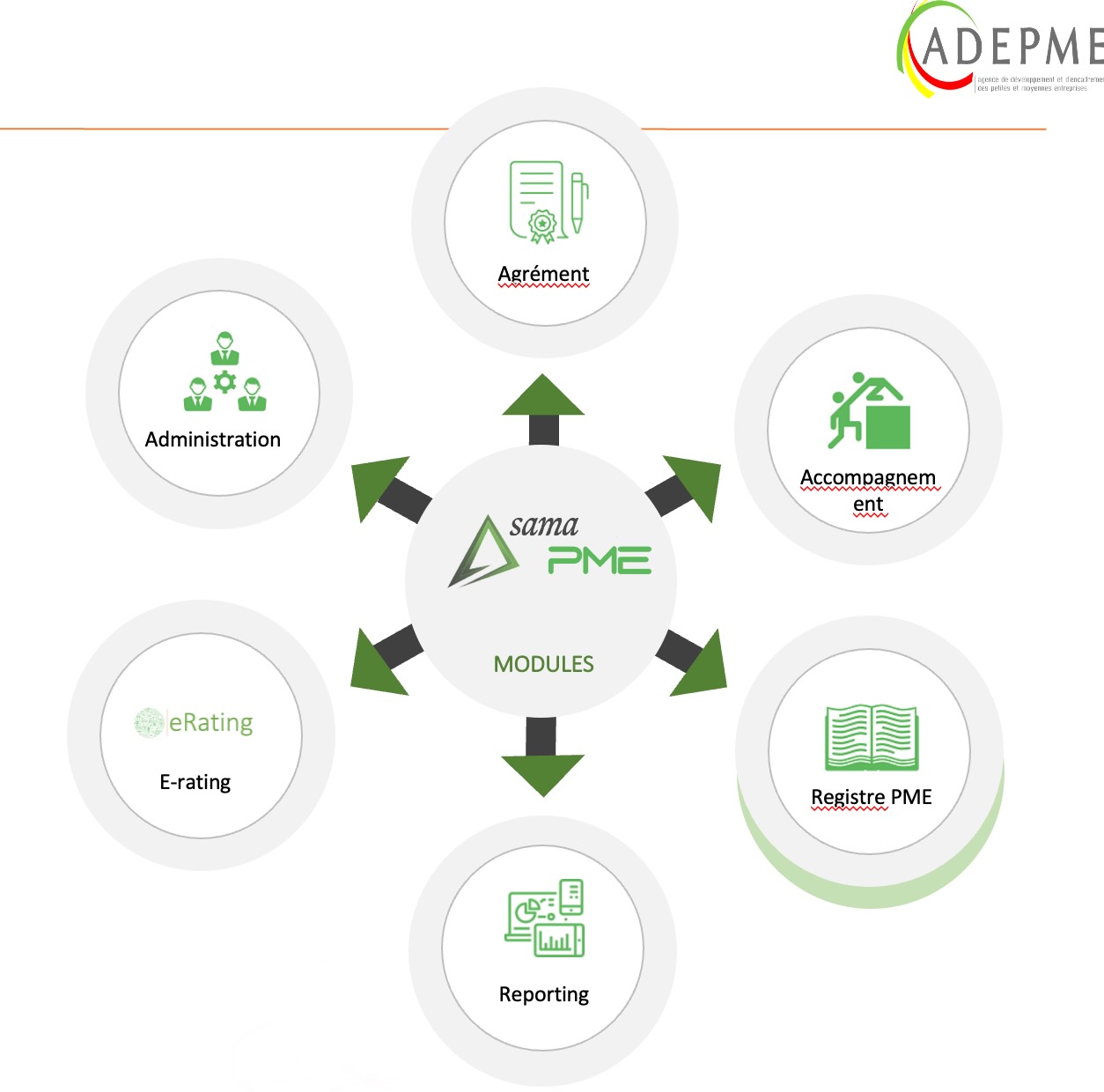





Comment travaillons nous